Definitions[]
A digital signature is
| “ | [d]ata appended to, or a cryptographic transformation of a data unit that allows a recipient of the data unit to prove the source and integrity of the data unit and protect against forgery e.g. by the recipient.[1] | ” |
| “ | an electronic signature based upon cryptographic methods of originator authentication, computed by using a set of rules and a set of parameters such that the identity of the signer and the integrity of the data can be verified.[2] | ” |
| “ | [a] method to authenticate digital materials that consists of an encrypted digest of the file being signed. The digest is an algorithmically-computed numeric value based on the contents of the file. It is then encrypted with the private part of a public/private key pair. To prove that the file was not tampered with, the recipient uses the public key to decrypt the signature back into the original digest, recomputes a new digest from the transmitted file and compares the two to see if they match. If they do, the file has not been altered in transit by an attacker.[3] | ” |
| “ | data that binds a sender's identity to the information being sent. A digital signature may be bundled with any message, file, or other digitally encoded information or transmitted separately. Digital signatures are used in public key environments and provide nonrepudiation and integrity services.[4] | ” |
Overview[]
| “ | A digital signature consists of three algorithms: (1) A key generation algorithm that selects a private key uniformly at random from a set of possible private keys. The algorithm outputs the private key and a corresponding public key. (2) A signing algorithm that, given a message and a private key, produces a signature. (3) A signature verifying algorithm that, given a message, public key, and a signature, either accepts or rejects the message's claim to authenticity. Two main properties are required. First, a signature generated from a fixed message and fixed private key should verify the authenticity of that message by using the corresponding public key. Secondly, it should be computationally infeasible to generate a valid signature for a party who does not possess the private key.[5] | ” |
In addition, a digital signature may be used to detect whether or not the information was modified after it was signed (i.e., to detect the integrity of the signed data). These assurances may be obtained whether the data was received in a transmission or retrieved from storage.
Digital signatures use public key cryptography to provide authentication, data integrity, and nonrepudiation for a message or transaction. Just as a physical signature helps to provide assurance that a letter has been written by a specific person, a digital signature helps provide assurance that a message was sent by a particular individual or machine. Digital signatures are often used in conjunction with a digital certificate.
A digital signature is a unique sequence of digits that is computed based on (1) the work being protected, (2) the digital signature algorithm being used, and (3) the key used in digital signature generation.[6] Generating a digital signature uses cryptographic techniques, but is not encryption of the work; the work may remain unencrypted so it can be accessed and used without decryption. In fact, digital signatures and encryption can be used simultaneously to protect works.
Mathematical algorithms can also be used to create digital signatures that, in effect, place a "seal" on a digitally represented work. Generating a digital signature is referred to as "signing" the work. The algorithms can be implemented through software or hardware, or both.
The digital signature serves as means for authenticating the work, both as to the identity of the entity that authenticated or "signed" it and as to the contents of the file that encodes the information that constitutes the work. Thus, by using digital signatures one will be able to identify from whom a particular file originated as well as verify that the contents of that file have not been altered from the contents as originally distributed.
Through the use of digital signatures, legally recognized signatures can be produced for use in electronic commerce. A digital signature is distinguished from an encryption product in that a digital signature does not provide confidentiality (i.e., does not prevent transmitted data from being monitored by unwanted parties).
The security of a digital signature system is dependent on maintaining the secrecy of the signatory’s private keys. Signatories must guard against the disclosure of their private keys.
Creating a digital signature[]
The creation of a digital signature can be divided into a two-step process based on public key cryptography. For performance reasons, public key cryptography is not used to encrypt large amounts of data. Therefore, the first step involves reducing the amount of data that need to be encrypted. This is typically accomplished by using a cryptographic hash algorithm, which condenses the data into a "message digest." Then the message digest is encrypted, using the sender’s private signing key to create a digital signature. Because the message digest will be different for each signature, each signature will also be unique; if a good hash algorithm is used, it is computationally infeasible to find another message that will generate the same message digest.
For example, if Bob wishes to digitally sign an electronic document, he can use his private key to encrypt the message digest of the document. His public key is freely available, so anyone with access to his public key can decrypt the document. Although this seems backward because anyone can read what is encrypted, the fact that Bob’s private key is held only by Bob provides the proof that Bob’s digital signature is valid.
Alice (or anyone else wishing to verify the document) can compute the message digest of the document and decrypt the signature using Bob’s public key. Assuming that the message digests match, Alice then has three kinds of security assurance. First, the digital signature ensures that Bob actually signed the document (authentication). Second, it ensures that Bob in fact sent the message (nonrepudiation). And third, because the message digest would have changed if anything in the message had been modified, Alice knows that no one tampered with the contents of the document after Bob signed it (data integrity). Of course, this assumes that (1) Bob has sole control over his private signing key and (2) Alice is sure that the public key she used to validate Bob’s messages really belongs to Bob.
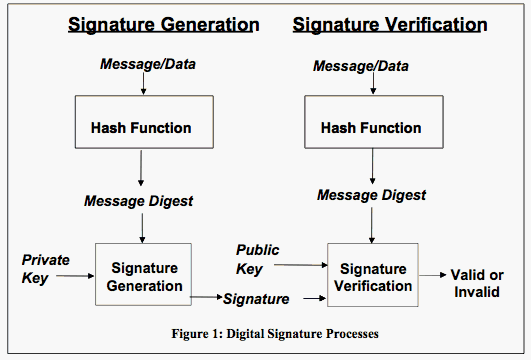
Signature generation/Signature verification[]
A digital signature algorithm includes a signature generation process and a signature verification process. A signatory uses the generation process to generate a digital signature on data; a verifier uses the verification process to verify the authenticity of the signature. Each signatory has a public and private key and is the owner of that key pair.
As shown in Figure 1 (below), the private key is used in the signature generation process. The key pair owner is the only entity that is authorized to use the private key to generate digital signatures. In order to prevent other entities from claiming to be the key pair owner and using the private key to generate fraudulent signatures, the private key must remain secret. The approved digital signature algorithms are designed to prevent an adversary who does not know the signatory’s private key from generating the same signature as the signatory on a different message. In other words, signatures are designed so that they cannot be forged.
An entity that intends to generate digital signatures in the future may be referred to as the intended signatory. Prior to the verification of a signed message, the signatory is referred to as the claimed signatory until such time as adequate assurance can be obtained of the actual identity of the signatory.
The public key is used in the signature verification process (see Figure 1 below). The public key need not be kept secret, but its integrity must be maintained. Anyone can verify a correctly signed message using the public key. For both the signature generation and verification processes, the message (i.e., the signed data) is converted to a fixed-length representation of the message by means of an approved hash function. Both the original message and the digital signature are made available to a verifier.
A verifier requires assurance that the public key to be used to verify a signature belongs to the entity that claims to have generated a digital signature (i.e., the claimed signatory). That is, a verifier requires assurance that the signatory is the actual owner of the public/private key pair used to generate and verify a digital signature. A binding of an owner’s identity and the owner’s public key must be effected in order to provide this assurance.
A verifier also requires assurance that the key pair owner actually possesses the private key associated with the public key, and that the public key is a mathematically correct key. By obtaining these assurances, the verifier has assurance that if the digital signature can be correctly verified using the public key, the digital signature is valid (i.e., the key pair owner really signed the message).
Digital signature validation includes both the (mathematical) verification of the digital signature and obtaining the appropriate assurances. The following are reasons why such assurances are required:
- If a verifier does not obtain assurance that a signatory is the actual owner of the key pair whose public component is used to verify a signature, the problem of forging a signature is reduced to the problem of falsely claiming an identity. For example, anyone in possession of a mathematically consistent key pair can sign a message and claim that the signatory was the President of the United States. If a verifier does not require assurance that the President is actually the owner of the public key that is used to mathematically verify the message’s signature, then successful signature verification provides assurance that the message has not been altered since it was signed, but does not provide assurance that the message came from the President (i.e., the verifier has assurance of the data’s integrity, but source authentication is lacking).
- If the public key used to verify a signature is not mathematically valid, the arguments used to establish the cryptographic strength of the signature algorithm may not apply. The owner may not be the only party who can generate signatures that can be verified with that public key.
- If a public key infrastructure cannot provide assurance to a verifier that the owner of a key pair has demonstrated knowledge of a private key that corresponds to the owner’s public key, then it may be possible for an unscrupulous entity to have their identity (or an assumed identity) bound to a public key that is (or has been) used by another party. The unscrupulous entity may then claim to be the source of certain messages signed by that other party. Or, it may be possible that an unscrupulous entity has managed to obtain ownership of apublic key that was chosen with the sole purpose of allowing for the verification of a signature on a specific message.
Using digital signatures to control copyrighted works[]
Generally, a signature is computed for a copyrighted work first and then the work (including the seal) is encrypted. When the work is to be used, the work is decrypted, then the signature (i.e., the seal) is verified to be sure the work has not been modified (either in its original or encrypted form). If the work is never changed, the seal need never be removed or changed. If the work is changed, a new seal must be computed based on the revised information.
Typically, the digital signature is incorporated in some manner in the transmission that constitutes the work. Often, the sender will also distribute his public key as well. The signature serves as a "seal" for the work because the seal enables the information to be independently checked for unauthorized modification.[7] If the seal is verified (independently computed signature matches the original signature), then the work is a bona fide copy of the original work — i.e., nothing has been changed in the file that constitutes the work.
References[]
- ↑ ITU, "Compendium of Approved ITU-T Security Definitizons," at 17 (Feb. 2003 ed.) (full-text).
- ↑ 21 C.F.R., Part 11, §11.3(5).
- ↑ NDSA Glossary.
- ↑ Privacy and Civil Liberties Policy Development Guide and Implementation Templates, App. E, Glossary.
- ↑ Criminal Justice Information Services (CJIS) Security Policy, Glossary, at A-5.
- ↑ The signature is generated using the binary digits of the work plus the value of the private key as inputs to the computation defined by the algorithm. Thus, the digital signature for an information object is a unique sequence of digits for that work. Specifically, a signature is not the same for different works using the same private key.
- ↑ Anyone who has access to an information object, in addition to having access to the work, also has access to the digital signature for the object. Consequently, the digital signature for the object may be recomputed and used to independently confirm the integrity of the object by comparing it to the digital signature appended to the object.