Overview[]
The National Commission on Terrorist Attacks Upon the United States (the 9/11 Commission) identified a breakdown in information sharing as a key factor contributing to the failure to prevent the September 11, 2001 attacks.
In response to the 9/11 Commission's Recommendations, the U.S. Congress passed and the President signed the Intelligence Reform and Terrorism Prevention Act of 2004 (IRTPA). This Act established the Information Sharing Environment (ISE) within the Office of the Director of National Intelligence.
Definition[]
The ISE is defined in the Act as
| “ | an approach that facilitates the sharing of terrorism and homeland security information, which approach may include any methods determined necessary and appropriate for carrying out this section. | ” |
Its principal goal is to enable and encourage the sharing of terrorism information in a manner consistent with national security and applicable legal standards relating to privacy and civil liberties. In practice, the ISE leverages existing capabilities by adjusting and integrating current policies, business processes, standards, and systems in order to improve information sharing among all ISE participants. The authors of IRTPA carefully avoided calling the ISE a “system” or “information sharing network.” The term “environment” was used to describe a virtual infrastructure or framework which enhances and streamlines information sharing in the Intelligence Community.
Duties of the ISE[]
Section 1016 of IRTPA requires the President to establish an Information Sharing Environment (ISE) for the sharing of terrorism information, weapons of mass destruction information, and homeland security information (herein referred to collectively as "terrorism-related information") in a manner consistent with national security and with applicable legal standards relating to privacy and civil liberties; designate the organizational and management structures that will be used to operate and manage the ISE; and determine and enforce the policies, directives, and rules that will govern the content and usage of the ISE.[1]
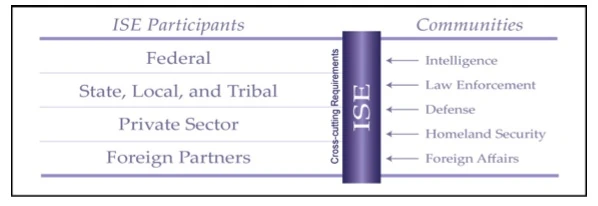
The IRTPA further requires that the ISE provide and facilitate “the means for sharing terrorism information among all appropriate Federal, State, local, and tribal entities, and the private sector”[2] and to the greatest extent practicable consist of “a decentralized, distributed, and coordinated environment” that:
- 1. Connects existing systems where appropriate, provides no single points of failure, and allows users to share information among agencies, levels of government, and, as appropriate, the private sector;
- 2. Ensures direct and continuous online electronic access to information;
- 3. Facilitates the availability of information in a form and manner that facilitates its use in analysis, investigations, and operations;
- 4. Builds upon existing systems capabilities currently in use across the Government;
- 5. Employs an information access management approach that controls access to data, rather than just systems and networks, without sacrificing security;
- 6. Facilitates the sharing of information at and across all levels of security;
- 7. Provides directory services, or the functional equivalent, for locating people, organizations, and information;
- 8. Incorporates protections for individuals’ privacy and civil liberties; and
- 9. Incorporates strong mechanisms to enhance accountability and facilitate oversight, including audits, authentication, and access controls.[3]
The Act required the President to designate a Program Manager for the ISE and establish an Information Sharing Council to advise the President and the Program Manager. The President’s Program Manager issued the ISE Guidelines to Ensure that the Information Privacy and Other Legal Rights of Americans are Protected in the Development and Use of the ISE (herein referred to as the "Privacy Guidelines"), which require relevant entities to have a written privacy protection policy that is at least as comprehensive as these guidelines. This document constitutes the Department of Homeland Security’s (DHS) Federal ISE Privacy and Civil Liberties Protection Policy (“Policy”).
Creating Fusion Center guidance and information sharing requirements[]
On December 16, 2005, President Bush issued a memorandum prescribing the guidelines and requirements supporting the creation and implementation of the Information Sharing Environment.[4] The President directed the heads of executive departments and agencies to work actively to create a culture of information sharing within their respective departments or agencies by assigning personnel and dedicating resources to terrorism-related information sharing. The President’s guidelines recognized that state, local, and tribal (SLT) authorities are critical to the nationwide efforts to prevent future terrorist attacks and are the first to respond when an attack occurs.
In August 2006, DHS and the Department of Justice published the Fusion Center Guidelines to help direct and provide assistance to developing fusion centers. These guidelines delineate 18 recommended elements for establishing and operating fusion centers. The guidelines are intended to improve consistency among the many different state and local fusion centers, enhance coordination, strengthen regional and national partnerships, and improve fusion center capabilities.
Developing a strategy for information sharing with Fusion Centers[]
In October 2007, the President issued the first National Strategy for Information Sharing[5] to prioritize and unify the Nation’s efforts to advance terrorism-related information sharing. The strategy integrates "Information Sharing Environment"-related initiatives and sets forth a national plan to build on progress made in improving information sharing and establishing an integrated national information sharing capability. The National Strategy emphasizes that information on homeland security, terrorism, and law enforcement related to terrorism can come from multiple sources and all levels of government.
The National Strategy designates fusion centers as vital assets critical to information sharing and anti-terrorism efforts, and as the primary state and local focal points for receiving and sharing of terrorism-related information. As a part of the National Strategy, the federal government recommends that fusion centers achieve a baseline capability level and become interconnected with the federal government and each other. This collaboration is intended to create a nationwide, integrated network of fusion centers to enable the effective sharing of terrorism-related information.
ISE Implementation Plan[]
The ISE Implementation Plan for the Information Sharing Environment sets forth the following vision:
| “ | A trusted partnership among all levels of government in the United States, the private sector, and our foreign partners, in order to detect, prevent, disrupt, preempt, and mitigate the effects of terrorism against the territory, people, and interests of the United States by the effective and efficient sharing of terrorism and homeland security information. | ” |
Realizing this vision will impact the numerous organizations participating in the ISE and will require achievement of the following six goals.
Privacy issues[]
ISE privacy and civil liberties objectives related to sharing terrorism information include:
- 1. Reviewing and adopting policies and procedures for handling protected information within the ISE and clarifying ISE participant responsibilities as custodians of that information;
- 2. Cataloguing agency data holdings to ensure that protected information that an agency makes available through the ISE has been lawfully obtained and made available consistent with authorized purposes;
- 3. Implementing mechanisms to enable ISE participants to determine the nature of the protected information that an agency is making available and to ensure it is handled in accordance with applicable legal requirements;
- 4. Adopting and implementing procedures to ensure the protected information is accurate and is not erroneously shared through the ISE;
- 5. Implementing appropriate physical, technical, and administrative measures to safeguard protected information shared through the ISE from unauthorized access, disclosure, modification, use, or destruction;
- 6. Developing policies and procedures for reporting, investigating, and responding to violations of policies and procedures regarding the handling of protected information;
- 7. Training personnel authorized to share protected information through the ISE on their agency's requirements and policies for the collection, use, and disclosure of protected information; and
- 8. Designating an ISE Privacy Official to receive reports and coordinate agency-specific privacy policies and procedures to ensure their consistency and compliance with ISE Guidelines.
The Program Manager for the ISE issued the Guidelines to Ensure that the Information Privacy and Other Legal Rights of Americans are Protected in the Development and Use of the ISE, which require relevant entities to have a written privacy protection policy that is at least as comprehensive as these guidelines.
References[]
- ↑ IRTPA §1016(b)(1)(A).
- ↑ Id. §1016(a)(2).
- ↑ Id. §1016(b)(2).
- ↑ “Memorandum for the Heads of Executive Departments and Agencies: Guidelines and Requirements in Support of the Information Sharing Environment,” Office of the Press Secretary, December 16, 2005 (full-text).
- ↑ National Strategy for Information Sharing: Successes and Challenges in Improving Terrorism-Related Information Sharing.