Definitions[]
A supervisory control and data acquisition system (SCADA system) is
| “ | [a] generic name for a computerized system that is capable of gathering and processing data and applying operational controls to geographically dispersed assets over long distances.[1] | ” |
| “ | [a] system of remote control and telemetry used to monitor and control the [electrical] transmission system.[2] | ” |
| “ | [a] [s]pecialized computer systems that monitor and control industrial processes, including the operation of components of the electric grid, by gathering and analyzing sensor data in near real time.[3] | ” |
Overview[]
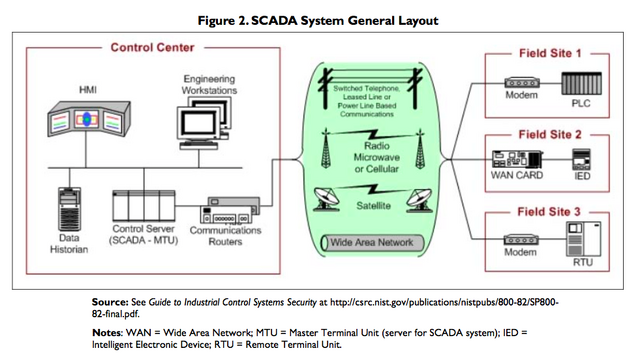
SCADA systems are highly distributed systems used to control geographically dispersed assets, often scattered over thousands of square kilometers, where centralized data acquisition and control are critical to [[system operation. . . . A SCADA control center performs centralized monitoring and control for field sites over long-distance communications networks, including monitoring alarms and processing status data. Based on information received from remote stations, automated or operator-driven supervisory commands can be pushed to remote station control devices, which are often referred to as field devices. Field devices control local operations such as opening and closing valves and breakers, collecting data from sensor systems, and monitoring the local environment for alarm conditions.
SCADA systems have been in use at least since the 1970s, and were adopted at a time when the focus of system design was on function and reliability. Historically, these systems consisted of remote terminal units15 which were often connected to a mainframe computer via telephone lines or radio connections. They were not typically connected to centralized networks. Utilities typically operated separate control systems created just to operate power plants and related infrastructure.
Components[]
A SCADA system is generally composed of six components: (1) instruments, which sense conditions such as pH, temperature, pressure, power level, and flow rate; (2) operating equipment, which includes pumps, valves, conveyors, and substation breakers; (3) local processors, which communicate with the site's instruments and operating equipment, collect instrument data, and identify alarm conditions; (4) short-range communication, which carry analog and discrete signals between the local processors and the instruments and operating equipment; (5) host computers, where a human operator can supervise the process, receive alarms, review data, and exercise control; and (6) long-range communications, which connect local processors and host computers using, for example, leased telephone lines, satellite, and cellular packet data.
Applications[]
SCADA are used in distribution systems such as water distribution and wastewater collection systems, oil and natural gas pipelines, electrical power grids, and railway transportation systems. A SCADA control center performs centralized monitoring and control for field sites over long-distance communications networks, including monitoring alarms and processing status data. Based on information received from remote stations, automated or operator-driven supervisory commands can be pushed to remote station control devices, which are often referred to as field devices.
Security issues[]
SCADA systems are computer systems relied upon by most critical infrastructure organizations to automatically monitor and adjust switching, manufacturing, and other process control activities, based on feedback data gathered by sensors. Some experts believe that these systems may be vulnerable to cyberattack, and that their importance for controlling the critical infrastructure may make them an attractive target for cyberterrorists.
SCADA systems once used only proprietary computer software, and their operation was confined largely to isolated networks. However, an increasing number of industrial control systems now operate using commercial-off-the-shelf (COTS) software, and more are being linked via the Internet directly into their corporate headquarters office systems. Some observers believe that SCADA systems are inadequately protected against a cyberattack, and remain vulnerable because many of the organizations that operate them have not paid proper attention to computer security needs.
| “ | Attacks on SCADA systems could obviously result in disruption of the network ("soft" damage), but because SCADA is used to control physical elements, such attacks could also result in irreversible physical damage. In cases in which backups for damaged components were not readily available (and might have to be remanufactured from scratch), such damage could have long-lasting impact.[4] | ” |
References[]
- ↑ NICCS, Explore Terms: A Glossary of Common Cybersecurity Terminology (full-text).
- ↑ U.S. Energy Information Administration, Glossary (full-text).
- ↑ Massachusetts Institute of Technology, The Future of the Electric Grid, Glossary, at 265 (2011) (full-text).
- ↑ Information Technology for Counterterrorism: Immediate Actions and Future Possibilities, at 20.
Source[]
- "Overview" section: NIST Special Publication 800-82.