Definition[]
Web 2.0 is a second generation method of using Web technology to create communities, or social networks, where instead of passively viewing content, each user can dynamically create, modify and share Web content. Web 2.0 technology allows users to collaborate and create self-organizing communities that can (1) increase the value and power of peer relationships and (2) simultaneously disrupt traditional real-world methods for hierarchical control over information flows.[1]
Overview[]
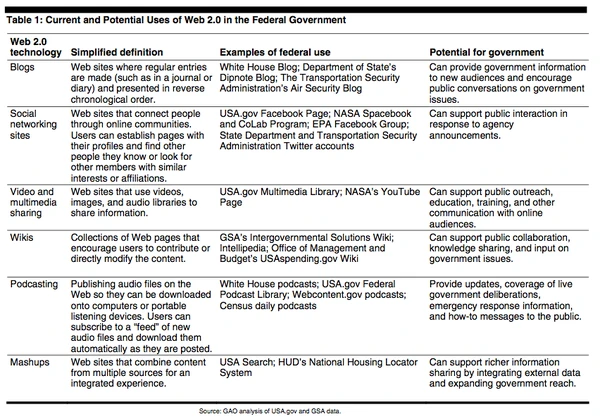
These technologies include Web logs (known as “blogs”); social-networking sites (such as LinkedIn, Facebook and Twitter), which also facilitate informal sharing of information; video-sharing websites (such as YouTube), which allow users to discover, watch, and share originally created videos; “wikis,” which allow individual users to directly collaborate on the content of Web pages (such as Wikipedia); “podcasting,” which allows users to download audio content; and “mashups,” which are websites that combine content from multiple sources.
While in the past Internet usage concentrated on sites that provide online shopping opportunities and other services, today video and social networking sites have moved to the forefront, becoming the two fastest growing types of websites in 2009, with 87% more users than in 2003. Furthermore, in February 2009, usage of social networking services reportedly exceeded Web-based e-mail usage for the first time. Similarly, the number of American users frequenting online video sites has more than tripled since 2003.
Corporate and government utilization[]
The decision to embrace social media technology is a risk-based decision, not a technology-based decision. It must be made based on a strong business case, supported at the appropriate level for each department or agency, considering its mission space, threats, technical capabilities, and potential benefits. The goal of the IT organization should not be to say “No” to social media websites and block them completely, but to say “Yes, following security guidance,” with effective and appropriate information assurance security and privacy controls.
The decision to authorize access to social media websites is a business decision, and comes from a risk management process made by the management team with inputs from all players, including the CIO, CISO, Office of General Counsel (OGC), privacy official and the mission owner.[2] The use of social media and the inherent cybersecurity concerns form a complex topic that introduces additional vulnerabilities, requiring updated sets of controls.
U.S. federal government[]
On January 21, 2009, President Barack Obama signed a Memorandum on Transparency and Open Government.[3] The Federal Government has responded with several initiatives which utilize collaborative social media technologies to engage with the public. The Federal CIO, Vivek Kundra, has stated Web 2.0 technologies are essential to "tap into the vast amounts of knowledge . . . in communities across the country."[4] Mr. Kundra has also developed a five-point plan to enable the administration's agenda: (1) open and transparent government; (2) lowering the cost of government; (3) cybersecurity; (4) participatory democracy; and (5) innovation.[5]
The use of social media technologies within the Federal Government quickly becomes a complex topic, with varying interpretations and perspectives. Researchers Dr. Mark Drapeau and Dr. Linton Wells at the National Defense University (NDU) define social media as social software, “applications that inherently connect people and information in spontaneous, interactive ways.” They have articulated four specific use cases of social media within the Federal Government.
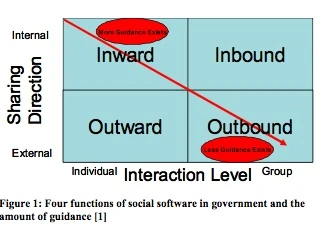
These four use cases, depicted in Figure 1, include Inward Sharing, Outward Sharing, Inbound Sharing, and Outbound Sharing. While related, each use case has different threats and requires different information security controls to mitigate those threats.[6]
- Inward Sharing is the sharing of internal organizational documents through internal collaboration sites such as SharePoint portals and internal wikis. As this is government information hosted on government or government-contracted information systems, it falls well within the definition of a federal information system under FISMA. Inward Sharing has quite a bit of guidance addressing system security, as shown in Figure 1.
- Outward Sharing, also known as inter-institutional sharing, enables Federal Government information to be shared with external groups, such as state and local governments, law enforcement, large corporations, and individuals. For example, agencies may use social media to communicate with the public during a time of crisis. Other examples of Outward Sharing include public websites used in a private function to facilitate the information-sharing role. These include GovLoop, an externally hosted social network catering to U.S. Government employees and contractors, STAR-TIDES, a knowledge-sharing research project for complex operations, and National Institute for Urban Search and Rescue, Readiness, Response, Resilience, and Recovery (NIUSR5) using LinkedIn to connect with members and share information.
- Inbound Sharing, also known as crowdsourcing, is similar to conducting a large online collaborative poll. Change.gov exemplifies inbound sharing where the “Open for Questions” forum allowed over 100,000 people to participate in a government-sponsored online meeting and submit over 75,000 questions ranging from the economy, to health care, to national security.
- Outbound Sharing is federal engagement on public commercial social media websites. The authors of the NDU document cite the example of Colleen Graffy, formerly the Deputy Assistant Secretary of State for Public Diplomacy, who used Twitter to connect with foreign media before her visits to their respective countries. This gave foreign media outlets a perspective into her personality before her arrival, called “Ambient Awareness,” and provided a human aspect to Ms. Graffy’s official role. Ultimately she enabled more comfortable communications during her trip, and received more favorable reviews by foreign media.
The use of social media and the subsequent cybersecurity concerns form a complex topic that involves, not only familiar threats, but also introduces additional vulnerabilities, targeted by an advanced threat, requiring updated sets of controls. There currently exists a robust set of computer security laws, policies, and guidance for federal information systems from NIST, DOD, OMB, GAO, and DHS.[7] Most of this guidance addresses federal information systems, which applies to internal information systems used for inward sharing. As federal agencies engage in external sharing with larger groups, the use case shifts toward outbound sharing on non-federal information systems, as demonstrated in Figure 1.
Less federal guidance exists for inbound, outward, and outbound sharing use cases, and the guidance that does exist is relatively recent. For example, the U.S. Air Force New Media Guide,[8] published in 2009, provides guidance to address these new use cases for the Federal Government.
Federal agencies are increasingly using Web 2.0 technologies to enhance services and interactions with the public. Federal Web managers use these applications to connect to people in new ways. As of July 2010, 22 of 24 major federal agencies had a presence on Facebook, Twitter, and YouTube.
References[]
- ↑ See Don Tapscott and Anthony Williams, Wikinomics (2006).
- ↑ A. Walls, "Corporate Use of Social Networks Requires Multilayered Security Control" (2007 Gartner Research).
- ↑ President Barack Obama, Memorandum on Transparency and Open Government (Jan. 21, 2009).[1]
- ↑ W. Kash, "Kundra: Government must tap into Web 2.0's potential," Fed. Computer Wk. (2009).[2]
- ↑ T. Newcombe, "Vivek Kundra, Federal CIO, Addresses State CIOs" (2009).[3]
- ↑ Mark Drapeau & Dr. Linton Wells, "Social Software and Security: An Initial ‘Net Assessment’" (2009 Center for Technology and National Security Policy, National Defense University, Washington, D.C.)
- ↑ Computer Security: A Summary of Selected Federal Laws, Executive Orders, and Presidential Directives.
- ↑ L. Clavette, et al., "New Media and the Air Force" (U.S. Air Force 2009).